Everything as Code: The Backbone of a Reliable, Secure, and Consistent DevSecOps Practice
At JPSoftWorks, you know, we've always believed that technology should serve people first: not the other way around. Over the years, working in SecDevOps, one truth has become increasingly clear to us: in order to create secure, maintainable, and high-quality systems, you need uniformity. And uniformity doesn’t happen by accident. It happens because you deliberately build it into your processes.
For us, one of the most powerful enablers of that uniformity is the philosophy of "Everything as Code" (EaC).
This isn’t just a catchy slogan or a trendy buzzword. It’s a disciplined approach that treats every element of your product lifecycle: application code, infrastructure, configurations, policies, pipelines, documentation, and even compliance checks: as version-controlled, reviewable, and testable artifacts.
And when you combine this philosophy with a solid Git-based branching and merging process, you unlock a level of consistency, traceability, and automation that fundamentally changes how you deliver value.
What "Everything as Code" Really Means
The simplest way to explain "Everything as Code" is:
If it can be expressed in a file, it belongs in version control. Ideally in a format that is friendly to content compares.
That means:
- Application code: of course, but also…
- Infrastructure as Code (IaC): Bicep, Terraform, ARM templates, Ansible playbooks, etc.
- Configuration as Code (CaC): Kubernetes manifests, application settings, feature flags.
- Policy as Code (PaC): Security and compliance rules, e.g., Open Policy Agent (OPA), Azure Policy definitions.
- Documentation as Code: Markdown, reStructuredText, or AsciiDoc files stored alongside the project.
- Pipeline as Code: CI/CD workflows in YAML (Azure DevOps, GitHub Actions, GitLab CI).
- Test definitions: Unit tests, integration tests, performance tests, and security scans scripts.
- Monitoring and alert definitions: Grafana dashboards, Prometheus rules, Azure Monitor alert definitions.
This approach eliminates the "special snowflake" problem: where production works one way, dev works another, and nobody’s quite sure how staging was set up. When everything lives in Git, there’s a single source of truth.
Why Git Is the Glue That Makes It Work
"Everything as Code" is powerful, but it’s not enough on its own. You need a discipline around how changes enter your codebase. That’s where Git, and specifically a deliberate branching and merging strategy, comes in.
We have a simple principle:
No change reaches the main branch without deliberate review and automated verification.
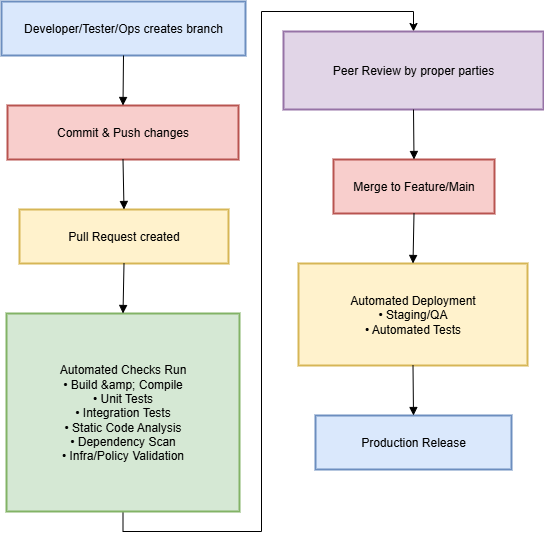
Every update: whether it’s a new feature, a change to infrastructure, a tweak in a policy, or a line in the documentation: comes in via a branch and a pull request (PR). That PR is the checkpoint where we:
- Review the change: human eyes on the code, by the right people.
- Run automated checks: tests, security scans, policy validations.
- Decide deliberately: to merge or not to merge.
It’s not just bureaucracy. This process is where we ensure that changes meet our standards for security, performance, compliance, and maintainability. It's one of the many ways, Security Developers and Operations, joion forces to arrive to a better quality product in record time.
Uniformity Through Review and Automation
An here's how it works.
When you have a Git/merge process in place, you build uniformity into your product for developers this has been a "no brainer".
This now becomes a practice spread in four key areas:
1. Product Consistency
Whether it’s application features or bug fixes, PR reviews ensure that:
- New code follows established patterns and coding standards.
- Functionality is consistent with business and user expectations.
- Security implications are addressed before code hits production.
Automated checks here might include:
- Compilation/build validation: make sure the code builds cleanly in a consistent environment.
- Unit tests: catch regressions early.
- Static code analysis: flag potential security vulnerabilities or bad practices (e.g., SonarQube, ESLint, Roslyn analyzers).
- Dependency scanning: identify vulnerable third-party packages.
2. Configuration Uniformity
Configuration drift is one of the biggest headaches in operations. With Configuration as Code:
- Your dev, QA, and production environments are built from the same base files.
- Any change in configuration goes through the same PR process.
- Rollbacks are as simple as reverting a Git commit.
Automated checks might include:
- Linting configuration files: e.g.,
yamllint,terraform validate. - Policy compliance: Azure Policy, OPA checks in pipelines.
- Idempotency tests: ensuring rerunning the configuration doesn’t cause unexpected changes.
3. Documentation Alignment
By keeping documentation in the same repo as the code, you eliminate stale, irrelevant, or contradictory docs.
- PR reviewers can check that documentation updates match the actual feature or configuration change.
- Automated processes can even check for broken links or missing sections.
- Tools like
mkdocsorSphinxcan automatically rebuild and publish updated documentation.
Automation here could include:
- Spellcheck/grammar check: automated linting for docs.
- Doc coverage checks: ensuring new features have accompanying documentation.
- Link validation: to ensure no outdated references.
4. Test Synchronization
Tests live alongside the code they validate. When you change a feature:
- The PR process requires updating or adding tests.
- Automated CI ensures those tests run on every change.
- Code coverage tools report if coverage has decreased.
This makes it impossible to "forget" to update tests because reviewers will catch it: and the pipeline will fail if the tests don’t pass.
The Automation Opportunities in the Merge Process
The pull request process is not just about human review. It’s also the perfect trigger point for automation. Our PR pipelines might run:
- Build & Compile: Verifying the code compiles in a clean environment.
- Unit Tests: Immediate validation of logic.
- Integration Tests: Ensuring services play well together.
- Static Code Analysis: Security and quality gates.
- Dependency Scans: SCA (Software Composition Analysis) to find vulnerable libraries.
- Infrastructure Validation: e.g.,
terraform planor Azure ARM/Bicep "What-If". - Policy Checks: Automated verification of security rules.
- Performance Baselines: Quick checks to ensure we haven’t introduced performance regressions.
- Compliance Verification: Automated SOC 2, ISO 27001, or internal policy checks.
- Container Image Scanning: Detect vulnerabilities in Docker images.
- Secret Detection: Prevent accidental commits of API keys or credentials.
This shift-left automation means issues are caught before they have a chance to impact production.
Security as an Embedded Outcome
Because everything goes through version control and PR review, we automatically embed security in the process:
- No undocumented changes: every change is tracked with commit history.
- No unauthorized changes: Git permissions enforce who can merge.
- Transparent audit trail: full visibility into who changed what and why.
- Security scans at PR time: so vulnerabilities are fixed before release.
In traditional environments, security is often a gate at the end of the pipeline. In "Everything as Code," security becomes part of the flow. This one of the key concepts.
Real-World Benefits
Implementing "Everything as Code" with disciplined Git processes gives JPSoftWorks and our clients:
- Fewer production incidents: because drift and undocumented changes are eliminated.
- Faster onboarding: new team members have the complete system described in code.
- Simpler audits: compliance evidence is in Git.
- Predictable deployments: what we tested is what we ship.
- Confidence in change: automated checks catch regressions early.
And perhaps the biggest benefit: trust. Teams trust the system because they know changes are deliberate, reviewed, and tested. Stakeholders trust delivery because they see a reliable track record.
Going Beyond: Future Opportunities
"Everything as Code" is not static. Here are some additional baby steps worth exploring:
- Automated threat modeling as part of PR pipelines.
- Self-healing infrastructure definitions that are triggered and adapt based on monitored metrics.
- AI-assisted PR reviews to flag potential issues faster.
- Unified observability as code: version-controlling dashboards and alert rules alongside application changes.
Conclusion
At JPSoftWorks, "Everything as Code" is more than a technical choice: it’s a cultural one. It says:
- We value transparency.
- We value deliberate change.
- We believe automation should amplify human expertise, not replace it.
- We believe that security, consistency, and quality are built in: not bolted on.
By combining the philosophy of "Everything as Code" with a disciplined Git-based merging process, we ensure that products, configurations, documentation, and tests evolve together: reviewed by the right people and validated by automation before they ever touch production.
That’s how we help create software that doesn’t just work today, but can be trusted tomorrow.
If you’d like to see how this approach can strengthen your own delivery processes: and secure them: let’s talk. At JPSoftWorks, we’re here to make tools and technology work for people, first. Contact Us




No comments:
Post a Comment